Overview: Automation in Cybersecurity Is No Longer Optional
By 2025, automation in cybersecurity will be essential rather than optional as cyber threats grow faster, smarter, and more complex. Reactive strategies are becoming outdated. To combat contemporary dangers and protect digital infrastructures, automation provides a proactive, scalable, and effective approach. This article delves deeply into how automation is changing cybersecurity, highlighting the main advantages, real-world applications, and strategic benefits that businesses can no longer afford to overlook.
Why Cybersecurity Technology Is Now Strategically Necessary
Cybercriminals are no longer lone hackers operating from basements—they are part of organized crime syndicates, state-sponsored groups, and automated botnets that work around the clock. Manual cybersecurity processes cannot keep pace with this level of sophistication and speed.
By 2025, the digital ecosystem includes cloud services, hybrid infrastructures, real-time data pipelines, and millions of connected devices. To secure such an environment, organizations must adopt automation in cybersecurity for continuous monitoring, real-time response, intelligent analysis, and compliance enforcement.
How Automation in Cybersecurity Works Across Key Domains
1. Threat Identification and Response
AI-powered systems detect anomalies in real-time:
- Review large logs within seconds
- Identify zero-day threats using behavioral models
- Automatically trigger alerts and mitigations
Example: An automated endpoint platform detects suspicious lateral movement and isolates affected nodes instantly.
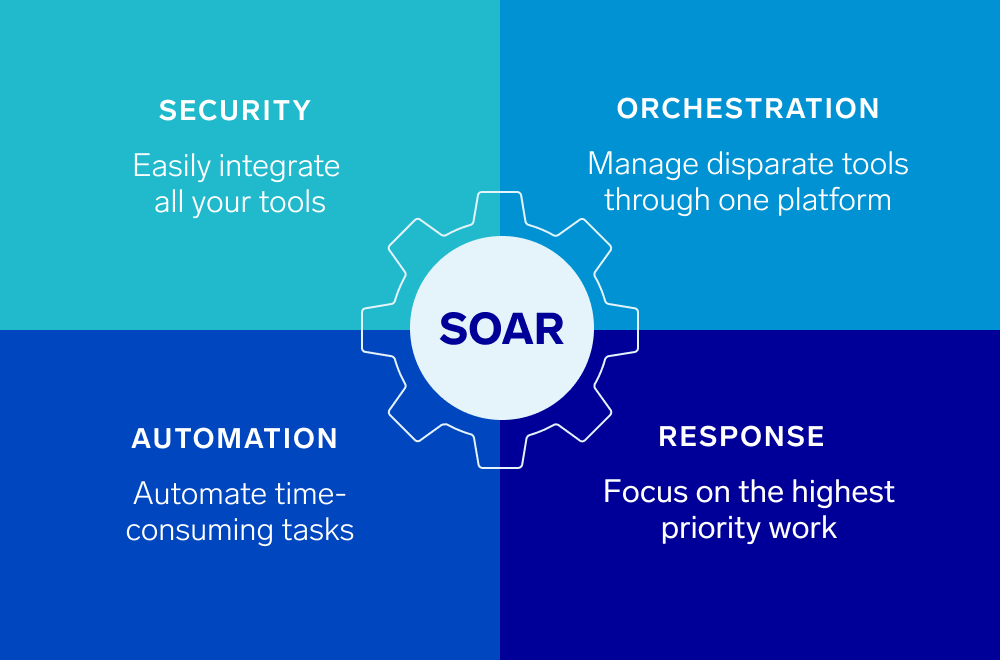
2. SOAR (Security Orchestration, Automation, and Response)
These platforms integrate multiple security tools and automate workflows:
- Centralize threat intelligence
- Minimize alert fatigue
- Auto-triage and respond to incidents
Use Case: A phishing email is detected, sandboxed, and removed from all inboxes; compromised credentials are disabled automatically.
3. Vulnerability Management & Patch Deployment
Automated scanners:
- Continuously assess systems
- Prioritize vulnerabilities
- Enable fast patch deployment
Effect: Drastically reduces time between detection and remediation.
4. Identity and Access Management (IAM)
Automated IAM ensures users only access what they need:
- Detect unusual access patterns
- Auto-deny or escalate suspicious login attempts
2025 Innovation: Context-aware automation flags anomalies and adjusts permissions in real time.
5. Compliance and Audits
Manual compliance is slow and error-prone. Automation ensures:
- Real-time policy enforcement
- Continuous audit trails
- Auto-generated compliance reports
Outcome: Faster audits and lower risk of regulatory penalties.
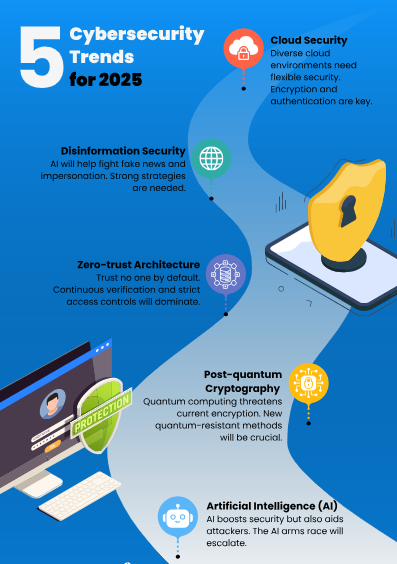
Key Benefits of Cybersecurity Automation in 2025
Cloud Security: Adaptive systems protect hybrid environments with encryption, access policies, and user behavior analytics.
Disinformation Defense: Detect and mitigate AI-generated fake content and impersonation threats.
Zero Trust Architecture: Constant validation of users and devices prevents unauthorized access.
Post-Quantum Cryptography: Future-ready encryption protects against quantum-enabled decryption.
AI Integration: Enhance defense capabilities while preparing for AI-powered threats.
Obstacles to Overcome in Automation Implementation
Notwithstanding the advantages, businesses need to deal with the following issues:
- Initial Investment & Integration Complexity: Connecting various security tools requires time and skilled resources.
- Risks associated with over-reliance: a blind reliance on automation without human supervision may result in mistakes in complex situations.
- Misconception of Security: Automation enhances human intelligence rather than replacing it. Better outcomes are guaranteed with a hybrid paradigm.
Long-term success depends on careful planning, testing, and ongoing observation.
How Big Businesses Are Using Automation Now
In 2025, top companies in several sectors are
- Implementing AI-driven SOAR platforms that process thousands of alerts and automatically close false positives.
- Using RPA (Robotic Process Automation) to manage access provisioning, log analysis, and phishing remediation.
- Deploying cloud-based automated compliance instruments to track the cloud’s setups, identity roles, and encryption policies in real time.
Improved MTTD (mean time to detect), MTTR (mean time to respond), and overall security posture resilience are reported by these companies.
Up-and-Coming Developments in Cybersecurity Automation for 2025
- Autonomous security agents are self-learning programs that can protect endpoints on their own.
- Automation-driven frameworks that change in response to threat intelligence and behavioral changes are known as adaptive security architectures.
- Enforcing Zero Trust: Automated systems provide least-privilege access in real time according to context.
- AI-Augmented Red Teaming: Artificial intelligence-planned attack scenarios to test defenses and identify blind spots.

Conclusion: Automation Is Today, Not the Future
Automation is more than simply tools in the cybersecurity landscape of 2025; it’s a change in perspective. It necessitates the design of both reactive and predictive systems. It requires businesses to adopt integrated workflows, real-time intelligence, and security that grows with complexity.
For organizations aiming to stay secure in this hyper-connected digital age, the path forward is clear: adopt automation, build intelligently, and remain resilient.