Must-Have Features in Enterprise Security Automation Platforms
In today’s evolving threat landscape, manual security operations are no longer sufficient. To stay ahead of increasingly sophisticated cyberattacks, enterprises are turning to security automation platforms. These platforms empower IT teams to proactively identify, respond to, and mitigate threats without constant human intervention.
But with dozens of tools available, how do you select the right one?
This blog outlines the key features you should look for in an enterprise security automation platform, ensuring your organization makes a smart, scalable investment.
Why Enterprises Need Security Automation
Today’s enterprises face thousands of alerts daily. Responding manually leads to fatigue, delays, and missed threats. That’s where automation comes in.
What Security Automation Can Do
- Reduce human error
- Accelerate incident response
- Enforce consistent policies
- Lower operational costs
📌 Internal Link: Learn how security automation trends are evolving in 2025
Key Features to Look for in Security Automation Platforms
Let’s dive into the must-have features that distinguish powerful, enterprise-grade automation tools.
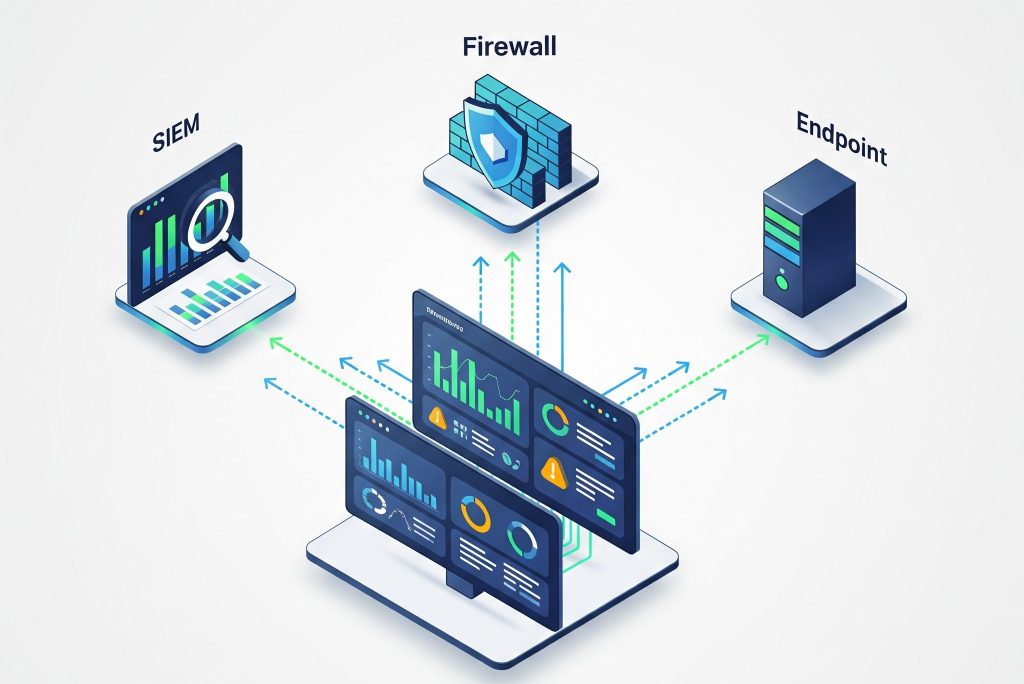
1. Integration with Existing Systems
Your chosen platform should seamlessly integrate with:
- Firewalls
- SIEM tools
- Endpoints
- Cloud platforms like AWS, Azure, and GCP
🔗 AWS Security Integration Docs
2. Low-Code/No-Code Workflow Builders
Look for platforms that offer drag-and-drop interfaces. These reduce the reliance on programming skills, making it easier for analysts to build and modify workflows.
💡 Tip: Drag-and-drop UI saves time and empowers junior security staff to contribute to automation.
3. Real-Time Threat Intelligence
A good platform should connect to external threat intelligence feeds like:
- IBM X-Force Exchange
- VirusTotal
- MISP
This helps in:
- Detecting zero-day attacks
- Correlating events
- Responding to known malicious IPs
4. Automated Incident Response Playbooks
The system must support reusable playbooks for common attack types such as:
- Phishing
- Ransomware
- Privilege escalation
Bonus if the platform allows customizable response steps based on severity levels.
5. Machine Learning & Behavior Analytics
Modern platforms now leverage ML to:
- Detect anomalies
- Identify insider threats
- Predict future attack vectors
Even better, some tools auto-adjust thresholds based on behavior patterns.
6. Role-Based Access Control (RBAC)
Enterprise systems must ensure only authorized personnel can modify automation rules or view sensitive alerts.
This aligns with Zero Trust Architecture, now essential in regulated industries.
🔗 Explore how zero trust is transforming modern cybersecurity
7. Dashboard & Reporting
Make sure the platform provides:
- Customizable dashboards
- KPI tracking (like MTTR, alert volume, false positives)
- Compliance-ready reporting formats (e.g., SOC 2, HIPAA, GDPR)
8. Cloud-Native & Scalable Infrastructure
Choose a platform built for the cloud to benefit from:
- Auto-scaling
- Global availability
- Microservices architecture
It should support both hybrid and multi-cloud environments.
Bonus Features Worth Considering
While not essential for all, the following features can offer competitive advantages:
- SOAR (Security Orchestration, Automation, and Response) Capabilities
- Built-in MITRE ATT&CK Framework Mapping
- Encrypted Logging and Immutable Audit Trails
- Mobile App Access for Alerts on the Go
Final Thoughts: Choose with Strategy
Security automation is more than just convenience—it’s a necessity in today’s high-risk environment. By selecting a platform with the right mix of integration, intelligence, and flexibility, your enterprise can stay protected without overburdening your teams.
As threats evolve, so should your tools.
So, before finalizing a security automation platform, evaluate how each feature aligns with your business’s long-term strategy.