Introduction: Why Ethical Hacking Matters More Today Than Ever
In today’s ultra-connected world, cyber threats are evolving faster than businesses can respond. Hackers no longer need physical access — a single vulnerability, misconfiguration, or weak password can expose an entire organization. Because of this, cybersecurity has become a top priority for businesses, governments, and startups worldwide. As cyberattacks grow, so does the demand for ethical hacking, a practice where trained professionals legally attempt to break into systems to make them more secure.
But the question remains:
Can hiring ethical hackers actually keep you safe?
The short answer is yes — when done correctly. Ethical hacking is not just an option anymore; it’s a necessity for surviving in the digital age. Many top organizations, including financial companies, healthcare systems, and SaaS businesses, now invest heavily in ethical hacking services because they uncover weaknesses before real criminals do.
Before diving deeper, let’s first understand what ethical hacking means, how it works, and why businesses trust hackers to secure their systems.
What is Ethical Hacking?
Ethical hacking refers to the authorized attempt to gain access to a system, network, or application to identify vulnerabilities before malicious attackers exploit them. Unlike criminal hackers, ethical hackers follow:
- Legal permissions
- Formal guidelines
- Professional security frameworks
- Signed contracts and NDAs
- Industry compliance requirements
They work to find security weaknesses in:
- Websites
- Mobile apps
- Cloud systems
- APIs
- Servers
- IoT devices
- Databases
- Internal networks
- Payment systems
Ethical hackers typically follow five major phases of hacking — but in a lawful and controlled manner.
The Five Phases of Ethical Hacking Explained
These structured phases ensure a complete security analysis.
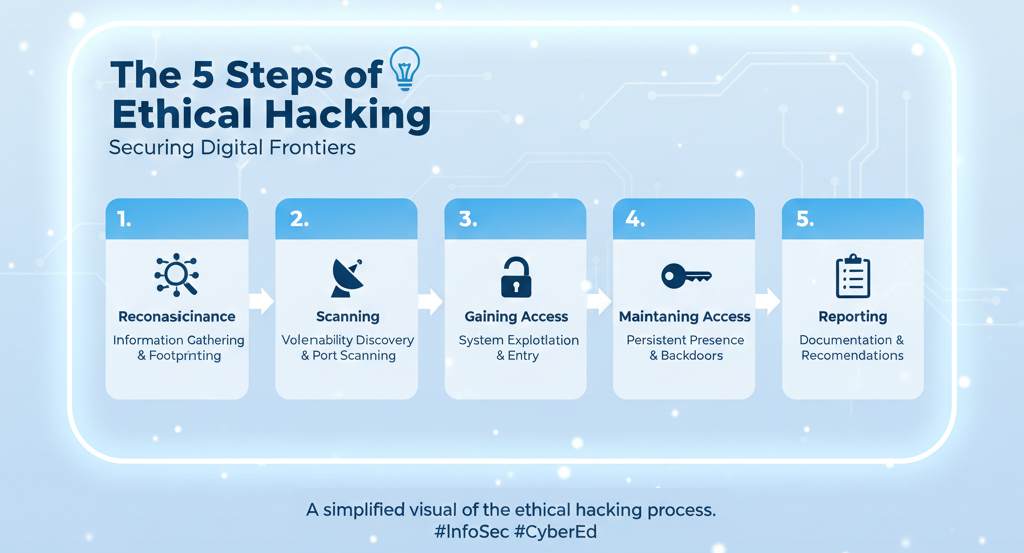
1. Reconnaissance (Information Gathering)
This is the stage where ethical hackers gather all possible information about the target system. They may use:
- OSINT (Open-Source Intelligence)
- Network scanning
- DNS interrogation
- Subdomain enumeration
- Data leak searches
The goal is to understand the attack surface.
2. Scanning & Enumeration
Here, hackers use automated tools to detect vulnerabilities. They analyze:
- Open ports
- Firewall rules
- Running services
- Software versions
- Entry points
This reveals what attackers might see if they target the system.
3. Gaining Access
Using controlled techniques, they attempt to exploit vulnerabilities like:
- SQL injection
- Cross-site scripting (XSS)
- Weak passwords
- Unpatched software
- Misconfigurations
This shows how deep an attacker could go.
4. Maintaining Access
Ethical hackers test whether attackers can remain inside the system without detection. This helps identify:
- Weak monitoring
- Poor logging
- Absence of intrusion detection systems
- Misconfigured alerts
5. Covering Tracks & Reporting
Instead of hiding their tracks for malicious intent, ethical hackers document everything and prepare a full report that includes:
- Findings
- Vulnerabilities
- Risk level
- Exploit details
- Impact analysis
- Recommended fixes
This report helps businesses strengthen security and avoid breaches.
Why Businesses Are Increasingly Hiring Ethical Hackers
As cybercrime reaches record levels, businesses are not waiting for an attack to occur. Instead, they invest in ethical hackers to proactively secure their systems.
Below are the top reasons companies hire ethical hackers.
1. Cyberattacks Are Becoming More Advanced
New forms of attacks like:
- Ransomware-as-a-Service
- AI-powered phishing
- Zero-day exploits
- Supply chain attacks
have drastically increased. To stay ahead, businesses need experts who understand attackers’ techniques — and ethical hackers are trained in exactly that.
2. Data Breaches Are Extremely Costly
According to global cybersecurity reports, data breach costs have crossed ₹40–50 crore on average for medium to large enterprises. Costs include:
- Legal fees
- Compliance penalties
- Loss of customer trust
- Reputation damage
- Business downtime
Ethical hacking is far cheaper than recovering from a breach.
3. Ethical Hackers Find Vulnerabilities Before Criminal Hackers Do
This is the biggest advantage. Ethical hackers simulate real-world attacks and find weak spots that businesses didn’t know existed. Their findings help organizations fix vulnerabilities proactively.
4. Compliance & Certifications Require Ethical Hacking
Many industries legally require security assessments:
- PCI DSS
- HIPAA
- ISO 27001
- GDPR
- SOC 2
Ethical hacking helps businesses achieve compliance and pass audits smoothly.
5. Startups Need Affordable Security
Startups often grow fast and deploy features quickly. This leads to security gaps. Ethical hackers help ensure that product speed doesn’t compromise user safety.
Types of Ethical Hackers: Which One Do You Need?
Ethical hackers come in different types, depending on how they operate.
1. White Hat Hackers
These are fully authorized professionals who work under strict guidelines. They follow rules and help organizations secure their systems legally.
2. Grey Hat Hackers
These individuals find vulnerabilities without permission but do not exploit them. They may report issues for recognition or reward. Companies must work with them carefully.
3. Bug Bounty Hunters
Many platforms and companies offer bug bounty programs where hackers report vulnerabilities in exchange for rewards. Even global companies like Google, Meta, and Microsoft run such programs.
A good example of bug bounty insights can also be found on Botdef’s blogs, such as one of their cybersecurity awareness articles on how automated threat detection helps prevent unknown vulnerabilities.
Ethical Hacking vs Malicious Hacking (Black Hat)
Understanding the difference helps organizations trust ethical hackers.

| Ethical Hackers | Malicious Hackers |
|---|---|
| Work legally with contracts | Work illegally |
| Protect systems | Break systems |
| Report vulnerabilities | Exploit vulnerabilities |
| Improve cybersecurity | Steal data, money, access |
| Paid by businesses | Paid by cybercrime |
Ethical hackers use the same tools and techniques as criminals — but for good.
How Ethical Hacking Keeps Your Business Safe
Let’s explore the real impact.
1. Identifies Weaknesses Before an Attack
Ethical hackers find vulnerabilities that may be invisible to internal teams.
2. Enhances Infrastructure Security
They test:
- Firewalls
- Routers
- Servers
- Cloud platforms
This ensures the whole stack is secure.
3. Reduces Security Risks
By identifying entry points, companies reduce their risk exposure drastically.
4. Prevents Data Leaks
Hackers test if personal or business data can be leaked through weak endpoints.
5. Tests Incident Response
Ethical hacking helps evaluate whether the team can detect and respond to real attacks quickly.

Key Ethical Hacking Techniques Used by Professionals
Ethical hackers use advanced techniques like:
- Vulnerability scanning
- Penetration testing
- Social engineering tests
- Red team operations
- API testing
- Wireless network testing
- Cloud penetration testing
Each technique reveals different layers of security.
Tools Used by Ethical Hackers
Some common tools include:
- Burp Suite
- Metasploit
- Nmap
- Nessus
- Wireshark
- Hydra
- Aircrack-ng
- OWASP ZAP
These tools help uncover vulnerabilities in multiple layers.
Real-World Examples of Ethical Hacking Success
Many companies have prevented massive data breaches thanks to ethical hackers. Organizations like banks, tech companies, and healthcare providers rely heavily on ethical hacking to protect their systems.
Large platforms such as e-commerce apps and payment gateways hire ethical hackers regularly to test their APIs and mobile apps. Even companies like Botdef rely on advanced cybersecurity practices to deliver safer environments for businesses across industries. Their cybersecurity solutions are designed to detect vulnerabilities early and automate threat prevention.
Should Small Businesses Hire Ethical Hackers?
Absolutely yes — because SMEs are the most targeted.
Reasons:
- They often have weak security
- They lack dedicated IT teams
- They rely heavily on digital payments
- They store customer data
- They cannot afford a breach
Hiring ethical hackers builds trust and safety.
How to Choose the Right Ethical Hacker or Agency
This is crucial.
1. Check Certifications
Look for qualifications such as:
- CEH (Certified Ethical Hacker)
- OSCP
- CompTIA Security+
- GIAC Penetration Tester
2. Check Experience
Ask for past reports (sanitized), tools used, and successful project references.
3. Check Legal Documentation
Ensure the agency signs:
- NDA
- Permission-to-test document
- Scope agreement
This protects both sides.
4. Check Their Cybersecurity Tools
Platforms like Botdef offer automated security tools that support professional hackers by monitoring threats 24/7.
Ethical Hacking Challenges
Even though ethical hacking is helpful, it comes with challenges:
- High cost for small businesses
- Limited scope if not planned well
- Risk of system disruption during tests
- Shortage of skilled ethical hackers
However, benefits outweigh the risks.
Future of Ethical Hacking
The future is bright due to:
- AI-powered pentesting
- Automated threat detection
- Zero-trust security models
- Cloud-based ethical hacking
- Continuous monitoring tools
- Bug bounty expansion
As AI evolves, so will hacking techniques. Ethical hackers will become even more essential for cybersecurity.
Conclusion: Can Hiring Ethical Hackers Actually Keep You Safe?
Yes — ethical hacking is one of the most effective ways to protect your business from cyber threats. Ethical hackers help detect vulnerabilities before criminals exploit them. They strengthen systems, improve monitoring, reduce risks, and enhance digital trust.
Whether you run a startup, enterprise, or growing company, hiring ethical hackers is not an option anymore — it is a necessity. Platforms like Botdef further support organizations through automated threat detection and advanced cybersecurity practices.
With cyber threats increasing every day, now is the perfect time to invest in ethical hacking and secure your future.