Introduction
In today’s fast-paced digital landscape, automation in patch management has become crucial, as unpatched software vulnerabilities remain a major entry point for cyber attackers. Manual patch management processes are often slow, error-prone, and unable to keep up with the sheer volume and frequency of new threats. Learn about NVD feeds. Automation addresses this gap by enabling organizations to detect, prioritize, test, and deploy patches across endpoints and systems with minimal human intervention. This not only reduces the risk of security breaches but also ensures faster compliance with industry standards and regulations.
Automated patch management improves visibility across IT infrastructure, supports real-time vulnerability scanning, and integrates with ITSM and DevOps workflows for seamless operations. By automating repetitive and time-sensitive tasks, IT teams can focus on higher-value strategic initiatives while keeping critical systems up to date and protected. As cyber threats become more sophisticated in 2025, automation has evolved from a convenience to a cybersecurity necessity.
Why Patch Management Matters
Vulnerabilities in security are unavoidable. Unresolved issues, however, provide hackers with an obvious route in, which is exactly what they want. Patch application delays result from:
- Legacy systems in complex IT settings
- Fear of interruptions or clashes with applications
- Inability to see all endpoints
- Manual procedures overburdened with documentation and approvals
These delays create “windows of opportunity” for attackers.
Imagine a system that, with the least amount of human intervention possible, finds vulnerabilities, assesses their seriousness, confirms compatibility, and applies remedies. Automated patch management promises that.
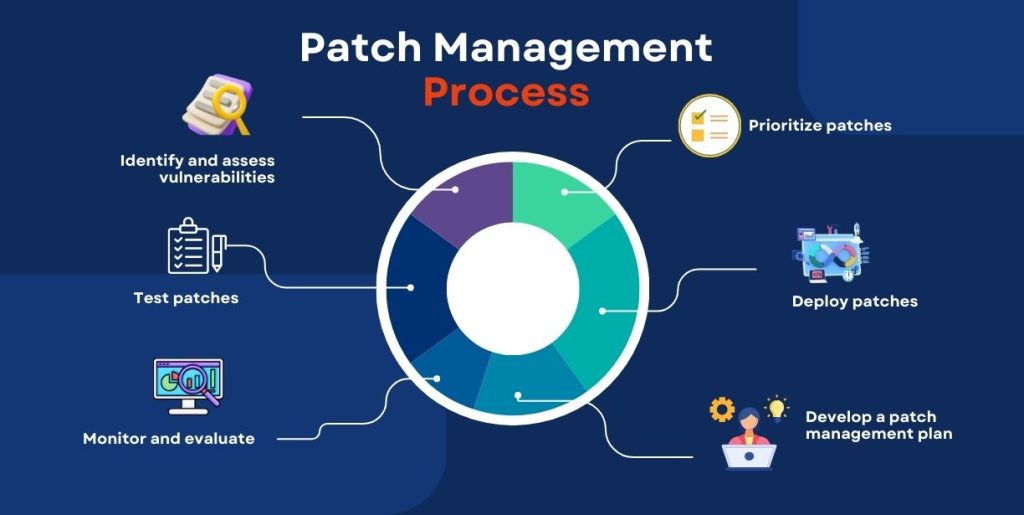
What Is Automation in Patch Management?
Automated patch management refers to the end-to-end coordination of finding, testing, and applying security updates across systems, devices, and cloud environments—with little to no human intervention.
It ensures that the appropriate patches reach the right systems at the right time and under the correct conditions—not just through automatic updates.
This includes:
- Automated identification of vulnerabilities.
- Prioritizing patches according to exposure and criticality
- Patch deployment in real time or on a schedule
- Plans for rollbacks and compliance checks
What sets automated solutions apart from conventional patching tools is this degree of orchestration.
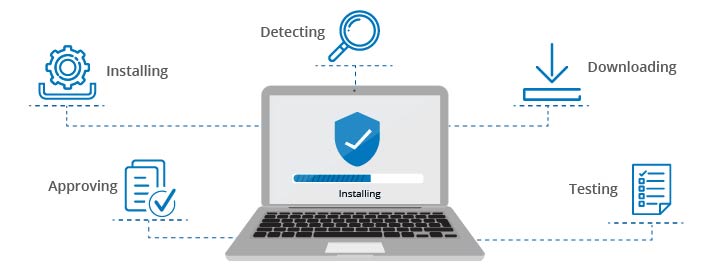
Step-by-Step Patch Automation Process
1. Identification and Inventory Charting
To know what to patch, automation tools continuously scan assets, software versions, and firmware across the infrastructure. These tools then map assets against known vulnerability databases (e.g., NVD, CVE feeds), eliminating blind spots.
2. Setting Priorities using Risk Intelligence
Not all vulnerabilities are equal. Automation platforms use threat intelligence, exploitability scores, and business context (e.g., whether a server is customer-facing) to rank patch urgency. This ensures critical vulnerabilities are addressed first.
3. Automated Testing & Sandbox Validation
Without testing, patch distribution might cause disruptions or break apps. Modern tools replicate system environments in sandbox labs, simulate patch behavior, & validate compatibility.
As a result, businesses are more assured that patches won’t interfere with operations, particularly in production systems.
4. Coordinated Environment-Wide Deployment
After testing, patches are released according to policy, either in rolling phases or during low-traffic periods. Updates are pushed to on-premise servers, external devices, and cloud workloads in a conflict-free manner.
5. Auditing and Reporting After Patches
After deployment, automation continues. In order to support compliance (HIPAA, ISO, SOC 2, etc.), it logs actions, monitors device states, and produces real-time data.
As a result, all of the patches are present. Instead of confusion, auditors are greeted with clarity.
Tools That Enable Patch Automation
Decades of apps and hundreds of endpoints are managed by large businesses. In these kinds of settings, manual patching is unscalable, slow, and prone to errors. The following benefits come with automation:
- Continuous vulnerability detection and reaction
- Mean Time to Patch (MTTP) is shortened from weeks to hours.
- Preventing service interruptions through planned deployment schedules
- Integration of ITSM platforms, such as ServiceNow, for workflows and ticketing
- CI/CD pipelines for automated container patching in alignment with DevOps
To put it another way, automation provides the three pillars of contemporary corporate defense: rapidity, visibility, and validation.
Important Security Automation Resources for Patch Management (2025)
While this blog focuses on process, it’s worth noting the tools empowering these capabilities:
- Patch Intelligence using Ivanti Neurons
- Patch Manager Plus by ManageEngine
- Patch Management for Qualys
- The Automox
- Microsoft Intune (Endpoint Manager included)
Each product offers pre-built policies and real-time dashboards and supports a variety of scenarios, including cloud-native, hybrid, and on-premises.
Obstacles to Think About—and Get Past
As with every change, there are challenges with automation:
- Automation agents might not be supported by legacy systems.
- Cultures with change control may oppose auto-deployment.
- Coverage may be compromised by fragmented IT visibility.
The answer? Begin with a staged strategy. Get visibility, start automating low-risk updates, and gradually spread trust to higher-tier systems.
Automated Patch Management’s Strategic Advantages
- Quicker Mitigation of Threats: Days after a vulnerability is revealed, exploits frequently occur. This window is nearly immediately closed by automation.
- Cutting Expenses: Reduces breach-related costs brought on by unpatched systems and eliminates expensive human labor.
- Confidence in Compliance: Keeps your systems up to date and your automated logs ready for audits.
- Operational Uptime: Planning ahead prevents service outages, which is essential for apps that interact with customers.
- Improved Posture for Security: Proactively manages risks for partners and stakeholders.
Explore Benefits of IT Process Automation
Final Thought: Speed, Security, and Automation
This old “patch when possible” mentality is no longer appropriate in an era where the assault landscape is changing hourly. Agility is necessary for cyber resilience, while automation is necessary for agility.
Organizations can turn patching from a bottleneck into a security enabler with the correct automated strategy, ensuring uptime, upholding confidence, and remaining one step ahead of attackers.
Not only is automation improving patch management, but it is also changing its rules.
Talk to us about patch automation: /contact-us








