Introduction: A New Dawn in Cloud Security
As cloud adoption skyrockets, so does the need for robust cybersecurity measures. Traditional threat detection methods are no longer enough to protect complex, distributed cloud systems. This is where automated threat detection steps in, offering real-time monitoring, AI-driven analysis, and scalable protection.
In this blog, we will explore the current trends, challenges, and the future of automated threat detection in cloud environments, and how it empowers enterprises to stay ahead of cyber threats.
🔐 Why Traditional Threat Detection Falls Short
Outdated Methods Can’t Keep Up
Manual threat detection systems rely heavily on predefined signatures and static rules. This approach:
- Struggles to detect zero-day threats
- Delays response time
- Requires heavy human intervention
Increased Attack Surfaces in the Cloud
With hybrid and multi-cloud infrastructures, the attack surface expands significantly, exposing more endpoints and entry vectors to attackers.
⚙️ What Is Automated Threat Detection in Cloud?
Automated threat detection leverages:
- Artificial Intelligence (AI) and Machine Learning (ML)
- Behavioral analytics and cloud-native security tools
- Threat intelligence feeds for continuous updates
👉 These systems learn from data, detect anomalies, and trigger responses instantly, even at scale.
🚀 Emerging Technologies Powering This Shift
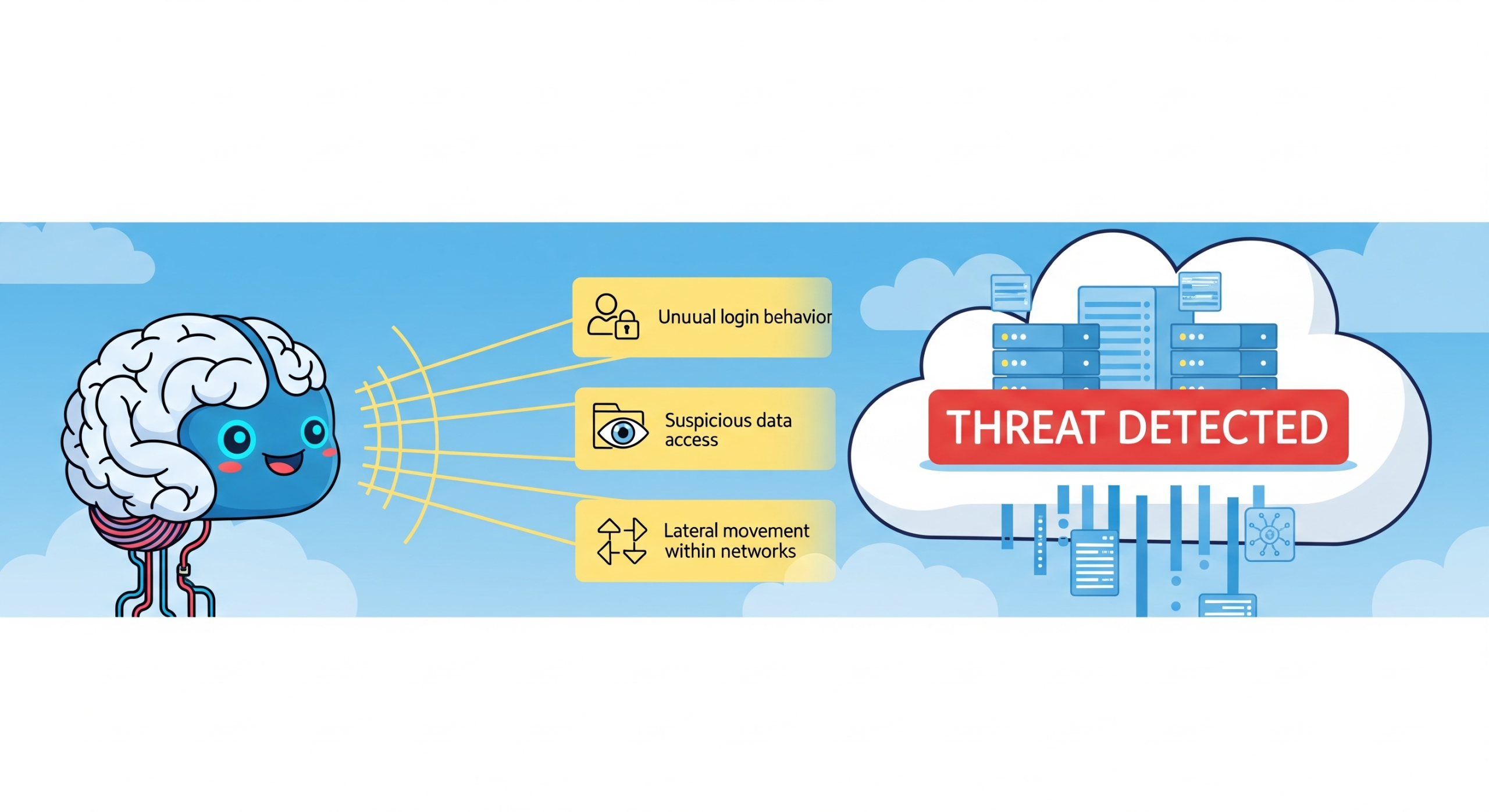
1. AI & Machine Learning Integration
Machine learning algorithms are capable of detecting patterns human analysts might miss. They identify:
- Unusual login behavior
- Suspicious data access
- Lateral movement within networks
2. SIEM & SOAR Integration
Security Information and Event Management (SIEM) tools, when integrated with Security Orchestration, Automation, and Response (SOAR) platforms, provide:
- Real-time data correlation
- Automated playbooks
- Instant incident response
🔗 Read more about SOAR tools and orchestration in our blog: Top Security Orchestration Tools for Enterprises
3. Cloud-Native Security Tools
Cloud providers offer built-in tools like:
- AWS GuardDuty
- Microsoft Defender for Cloud
- Google Chronicle
These tools provide out-of-the-box integration with cloud assets for faster threat detection and reduced manual configuration.
📊 Key Benefits of Automated Threat Detection
Real-Time Monitoring
Constantly watches over cloud workloads without human involvement.
Scalability
Easily handles large-scale infrastructures and fluctuating workloads.
Proactive Threat Hunting
Instead of just reacting, these tools predict and prevent attacks before they occur.
Reduced False Positives
ML algorithms refine alert accuracy, helping security teams focus on real threats.
⚠️ Challenges Ahead
While promising, there are challenges that still need attention:
- Data Privacy & Compliance: GDPR and HIPAA require careful handling of automated monitoring.
- High Initial Setup Cost: Automation requires investment in tools and training.
- Skill Gap: Teams need upskilling in AI/ML-based SecOps practices.
📈 The Road Ahead: What the Future Holds
Autonomous Security Agents
We’re moving toward fully autonomous agents that take actions like isolating compromised instances or quarantining traffic.
Context-Aware Threat Intelligence
Future systems will use contextual awareness to understand business logic, reducing false positives and increasing actionable insights.
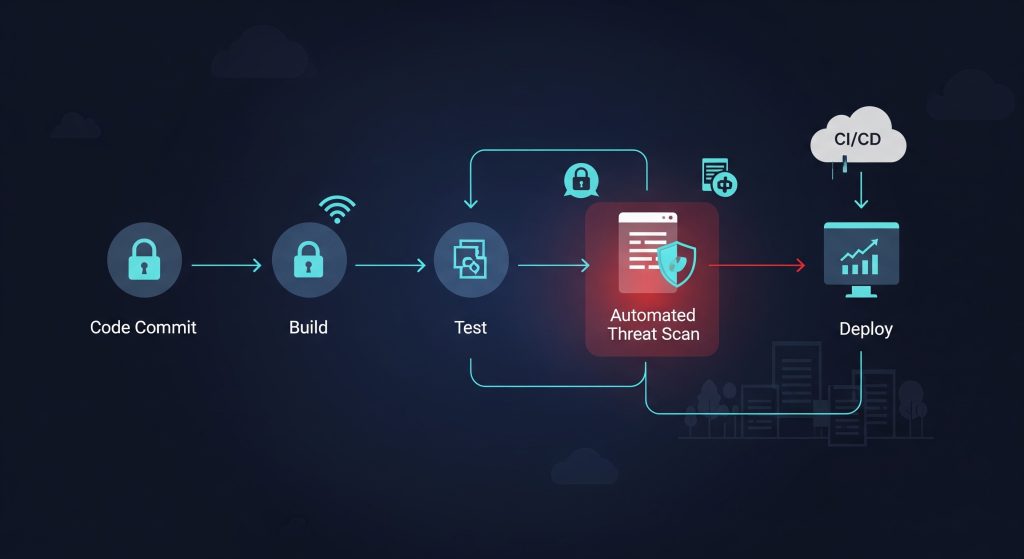
Integration with DevSecOps
Threat detection will become embedded in CI/CD pipelines, enabling security as code in real-time.
✅ Best Practices to Prepare for the Future
- Invest in AI and ML-powered security platforms
- Shift from reactive to proactive security postures
- Train your SecOps team on cloud-native tools
- Regularly audit and update security playbooks
- Leverage automation pipelines for threat response
Conclusion: Automation Is Not the Future—It’s the Present
To stay resilient against ever-evolving cyber threats, organizations must embrace automation in threat detection today. As cloud environments grow more complex, relying on manual or traditional security methods is no longer viable.
Instead, organizations should invest in smart, scalable, and responsive automated systems that align with the future of cloud security.
🔗 Gartner: Top Trends in Cloud Security