Introduction: Understanding the Core of Cybersecurity Teams
In today’s threat-filled digital ecosystem, cybersecurity isn’t just a department — it’s a battlefield. To protect digital infrastructure, organizations deploy structured teams with distinct roles and mindsets. These teams are commonly known as the Red Team, Blue Team, and Purple Team.
Each plays a unique yet interconnected role in strengthening security systems. While the Red Team simulates real-world attacks, the Blue Team defends and detects breaches, and the Purple Team unites both for enhanced collaboration.
At BotDef, we believe a balanced security strategy involves the perfect synergy between these three teams to achieve continuous defense readiness.
What Is the Red Team in Cybersecurity?
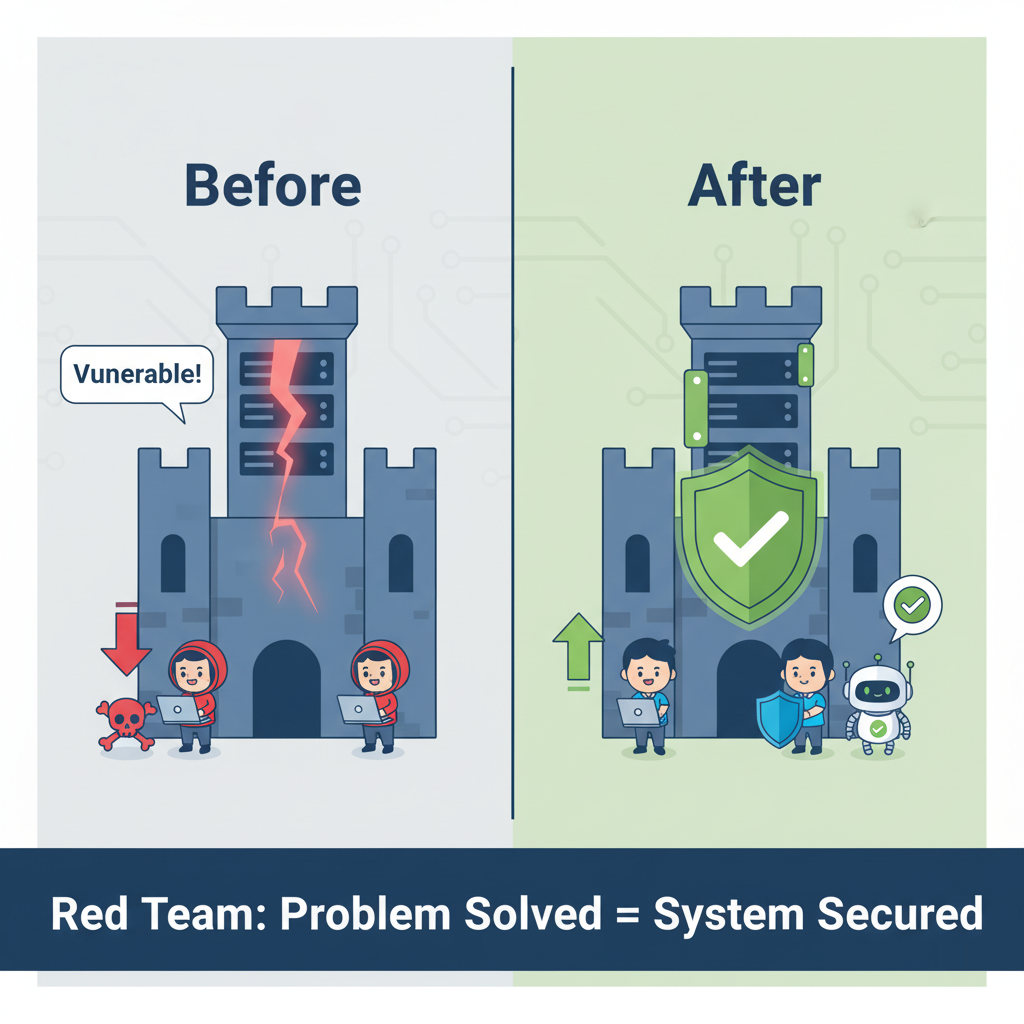
The Red Team consists of ethical hackers or penetration testers who act as attackers. Their mission is to mimic real-world cyber threats, uncover vulnerabilities, and test how resilient your systems truly are.
Key Responsibilities of the Red Team
- Conduct simulated cyberattacks to assess security posture.
- Exploit system, network, and application vulnerabilities.
- Identify weak points in human behavior via phishing or social engineering.
- Provide post-assessment reports with improvement suggestions.
💡 Example: Suppose your organization’s web application has a hidden vulnerability. The Red Team will exploit it to show how a real hacker could breach your network — giving you a chance to patch it before it’s too late.
What Is the Blue Team in Cybersecurity?

The Blue Team represents the defenders — the experts responsible for detecting, analyzing, and mitigating attacks in real time. Their work revolves around continuous monitoring, log analysis, and incident response.
Key Responsibilities of the Blue Team
- Monitor networks for suspicious activities.
- Strengthen firewalls, IDS, and security configurations.
- Respond to alerts and manage incident recovery.
- Conduct regular security audits and risk assessments.
💡 Example: When the Red Team launches a simulated phishing attack, the Blue Team must detect and neutralize the threat — ensuring no sensitive data is leaked.
The Purple Team – A Bridge Between Red and Blue
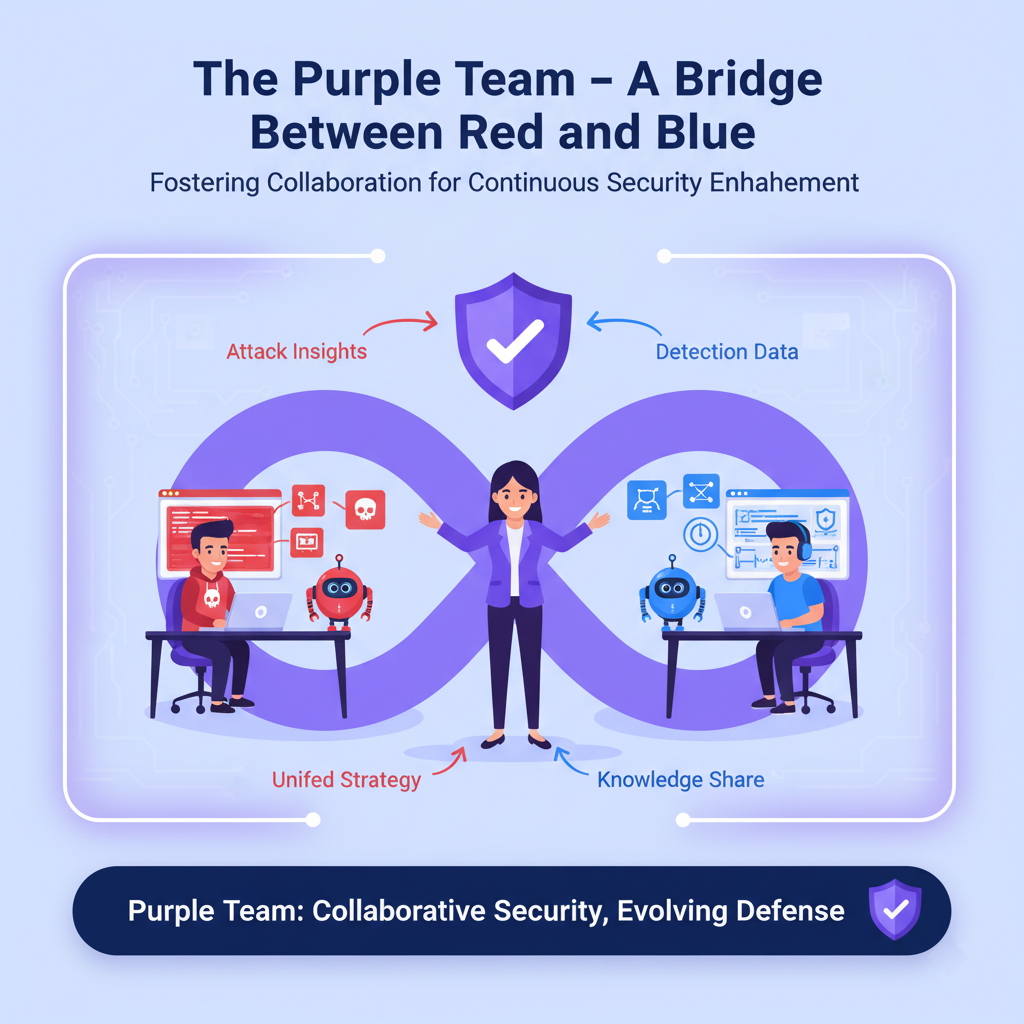
The Purple Team combines the best of both worlds — offensive and defensive. Their goal is to foster collaboration and transparency between Red and Blue Teams to maximize the effectiveness of security measures.
Key Responsibilities of the Purple Team
- Facilitate communication between attackers and defenders.
- Share insights from Red Team assessments with Blue Teams.
- Create continuous improvement feedback loops.
- Optimize tools, strategies, and response frameworks.
💡 Example: After a Red Team attack simulation, the Purple Team holds a debrief session with both teams to analyze what worked, what failed, and how defenses can be improved.
Key Differences Between Red, Blue, and Purple Teams
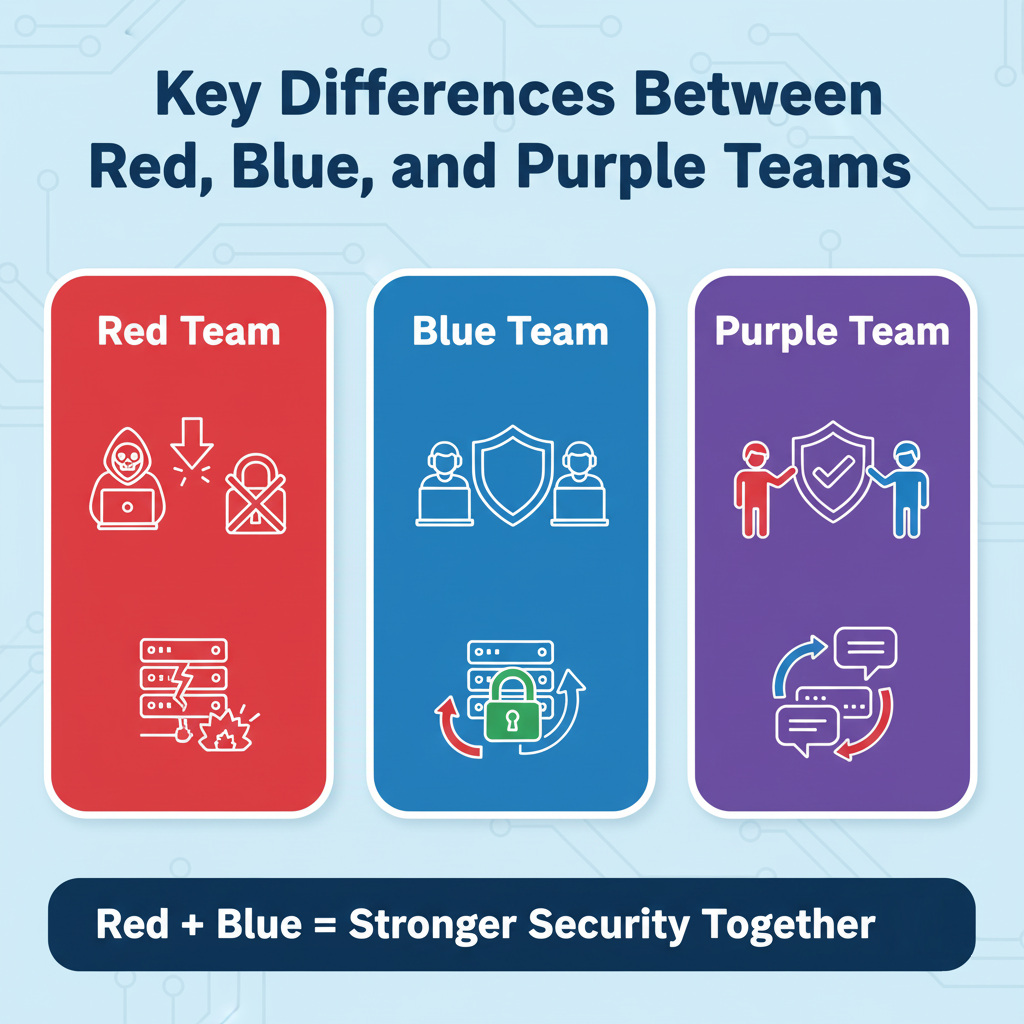
| Aspect | Red Team | Blue Team | Purple Team |
|---|---|---|---|
| Objective | Offensive – Simulate attacks | Defensive – Protect and respond | Collaborative – Enhance both |
| Approach | Ethical hacking, penetration testing | Threat detection, incident response | Knowledge sharing, coordination |
| Skill Focus | Exploitation, OSINT, social engineering | Monitoring, forensics, analysis | Strategy alignment, communication |
| Tools | Metasploit, Burp Suite | SIEM tools, firewalls, IDS | Combined toolsets and feedback loops |
Why a Collaborative Approach Matters
Cyber threats are evolving faster than ever. A standalone Red or Blue Team is no longer sufficient. Organizations that integrate both offensive and defensive operations — via the Purple Team — gain real-time adaptability and insight.
At BotDef, we specialize in automated threat simulation and defense readiness platforms that align with Red, Blue, and Purple Team methodologies.
Visit BotDef.com to explore how our cybersecurity automation tools enhance your organization’s threat intelligence.
Learn more about cybersecurity team structures from Cybersecurity & Infrastructure Security Agency (CISA).
Final Thoughts
In summary, the Red Team, Blue Team, and Purple Team aren’t competitors — they’re collaborators working toward the same mission: securing digital ecosystems. By understanding each team’s role and fostering synergy, businesses can detect, prevent, and respond to cyber threats more effectively.
Implementing this tri-team strategy with the support of BotDef ensures your organization stays one step ahead in the cybersecurity race.