Overview: Why Security Automation Tools Matter in 2025
In 2025, security automation tools are no longer just an advantage—they are a necessity. With hybrid work, cloud-first strategies, and constant threats, the demand for scalable, integrated, and intelligent defense solutions has skyrocketed.
This blog explores the top 5 security automation tools in 2025 that every business should know, along with must-have features, use cases, and why these tools are reshaping cybersecurity operations.
What Makes a Tool Enterprise-Ready?
Before we explore the tools, here’s what to look for in security automation tools 2025:
- Scalability – Can handle thousands of events in real-time.
- Integration – Works with SIEM, SOAR, IAM, cloud, DevOps.
- AI/ML-Driven – Can think, adapt, and evolve.
- Orchestration Support – Runs complex playbooks and automations.
- Compliance – Supports ISO 27001, HIPAA, GDPR, etc.
1. Splunk SOAR
Where Intelligence Meets Orchestration
Splunk SOAR (formerly Phantom) is a leading security automation tool combining machine learning with low-code playbooks.
Key Features:
- 300+ third-party integrations
- Visual playbook builder
- Automated threat scoring
- Incident triaging without analyst intervention
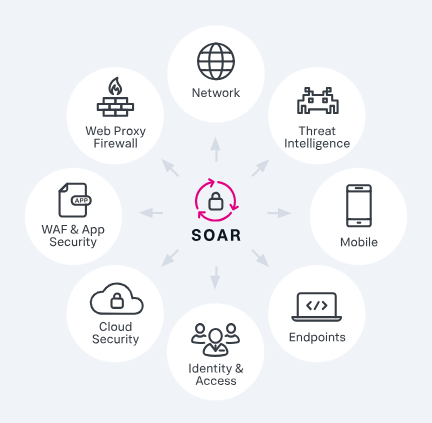
Use Case: Automatically handles phishing alerts, classifies them, and updates firewall rules instantly.
2. Cortex XSOAR by Palo Alto
Enterprise-Grade Threat Response
Cortex XSOAR is an intelligent SOAR platform combining incident response with threat intelligence.
Key Features:
- 700+ security integrations
- In-built War Room for live collaboration
- Dynamic case management
- Automated ticketing
Use Case: Detects ransomware, isolates hosts, notifies teams, and restores backups—all in seconds.
3. Tines
No-Code Automation for Everyone
Tines allows security teams to automate without writing code. It’s highly visual and easy to adopt.
Key Features:
- Drag-and-drop interface
- Behavior-based logic triggers
- Slack, AWS, Jira, Sentinel integrations
Use Case: Scans domain reputations and raises automated alerts for high-risk sites., and auto-generates Jira tickets for high-risk findings.
4. Swimlane Turbine
Cloud-Native Security Automation at Scale
Swimlane Turbine offers low-code orchestration, real-time ingestion, and edge-to-cloud automation.
Key Features:
- Kubernetes-native
- Federated case management
- Advanced normalization of security events
Use Case: Monitors 10,000+ endpoints, halts malicious sessions in real time.ational e-commerce company to keep an eye on over 10,000 endpoints. The system correlates logs, identifies irregularities, and immediately stops malicious sessions.
5. Microsoft Sentinel (w/ Logic Apps)
Seamless SIEM + Automation for Azure Ecosystem
Microsoft Sentinel, paired with Logic Apps, offers scalable SIEM and security automation.
Key Features:
- Native Azure integrations (AD, Defender)
- ML-based anomaly detection
- Policy-based incident response
Use Case: Detects suspicious logins and enforces MFA or blocks access instantly.
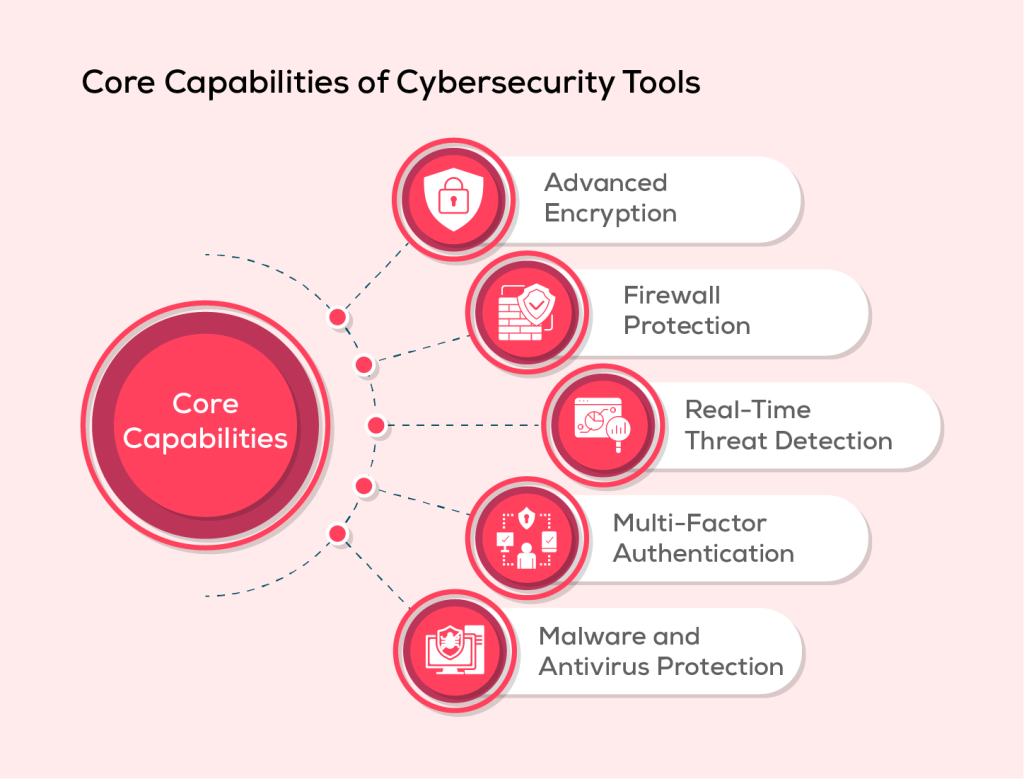
Key Technologies Supporting These Tools
🔐 Encryption: Protects sensitive data during transit and storage.
🧱 Firewall Defense: Blocks unauthorized traffic to internal networks.
⚠️ Real-Time Threat Detection: Proactive monitoring for anomalies.
🔐 Multi-Factor Authentication (MFA): Enhances identity protection.
🛡️ Anti-Malware & Antivirus: Detects and neutralizes malware before impact.
How to Choose the Right Security Automation Tool
When evaluating security automation tools in 2025, consider:
✅ Your organization’s threat landscape
✅ Integration with existing infrastructure
✅ Compliance requirements (HIPAA, ISO27001, GDPR)
✅ Tool scalability & user-friendliness
✅ Cost vs. ROI
You can also check out our latest blog on DevOps automation for related insights.
Conclusion: Automation Is the New Norm in Security
Security isn’t just about detection anymore—it’s about automated defense. From cloud-native orchestration to no-code incident response, security automation tools in 2025 are reshaping how businesses fight cyber threats.
✅ Automate
✅ Scale
✅ Secure
The businesses that adapt early will build resilience and reduce risk faster than those who lag behind.