Introduction: A Year of Cybersecurity Development
The field of cybersecurity is evolving rapidly, and in 2025, security automation trends are reshaping how organizations detect and respond to threats. Manual techniques are no longer adequate to guarantee real-time threat detection, quick response, and ongoing compliance as assaults become more complicated and frequent. Modern cybersecurity frameworks are increasingly built on security automation, which streamlines everything from handling patches to handling emergencies.
Ten of the most significant security automation trends that are anticipated to shape cybersecurity in 2025 are explored in this blog. These trends are not merely forecasts; they are currently happening and have an impact on how companies design their digital defenses.
1. Self-governing Threat Identification and Reaction Mechanisms
Traditional SIEM (security information and event management) technologies are being replaced by AI-powered solutions that can recognize and eliminate threats on their own. Without human assistance, these systems examine baselines in behavior, identify irregularities, and carry out preset reactions.
This evolution means organizations no longer have to wait for human analysts to flag threats—AI-based solutions can detect malware, lateral movement, and exfiltration patterns within seconds.
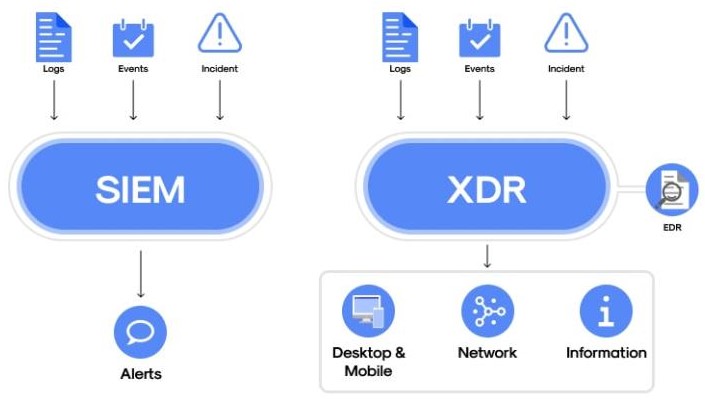
2. AI-Augmented Security Operations Centers (SOCs)
AI-augmented command centers, where AI serves as a real-time co-pilot to human analysts, are replacing security operations centers. The main benefit? Drastically reduced mean time to detect (MTTD) and mean time to respond (MTTR)
The automation of Level 1 and Level 2 triage activities allows security analysts to concentrate on compliance, criminal investigations, and global threat hunting.
3. Security-as-Code: DevSecOps Automation’s Ascent
By 2025, security is an integral part of the software development process. Safety as Code integrates automated compliance, vulnerability scanning, and secret detection at every CI/CD stage. Code embeds policies directly into pipelines.
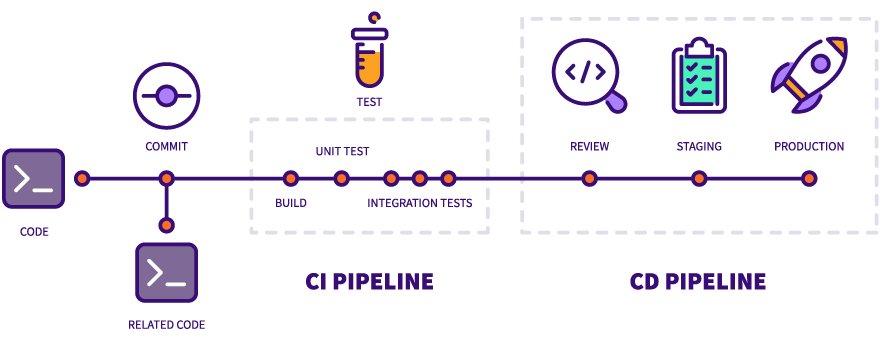
These days, security automation solutions offer developers real-time feedback and immediately stop dangerous builds.
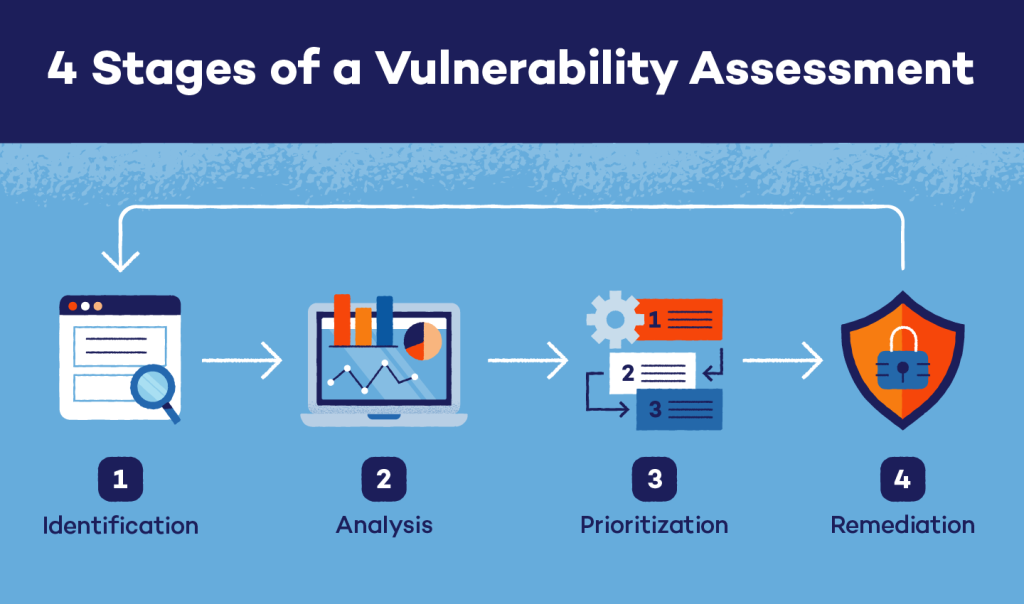
4. Patch and Vulnerability Management Automation
Traditionally, patch management has been a laborious, manual process. Automated patch orchestration solutions have made it possible for enterprises to guarantee prompt patching of zero-day vulnerabilities without interfering with daily operations.
Patches are prioritized according to risk scores, tested in sandbox settings, and then distributed throughout hybrid infrastructures using these techniques.
5. Automating Zero Trust Using Dynamic Access Controls
Automating the process is redefining zero trust concepts. In 2025, identity, behavior, location, and device health are evaluated in real-time to grant or deny access dynamically.
With the use of AI and behavioral analytics, this flexible strategy lessens insider threats and stops lateral network migration.
6. Cloud Security Posture Management (CSPM) Automation
Misconfigurations in cloud security remain a major source of intrusions. These days, CSPM technologies have automatic policy enforcement, cloud environment scanning, and the ability to fix problems like weak roles for IAM or empty S3 buckets.
In hybrid and multi-cloud settings, this automation guarantees ongoing conformance to frameworks such as NIST or CIS Benchmarks.
7. Using Robotic Process Automation (RPA) in Security Procedures
RPA isn’t just for HR and finance—it’s revolutionizing security operations. Bots are automating repetitive security operations on servers and endpoints, such as retrieving threat intelligence reports and sending out email notifications.
By automating repetitive procedures, security analysts may concentrate on essential decision-making and reaction preparation.
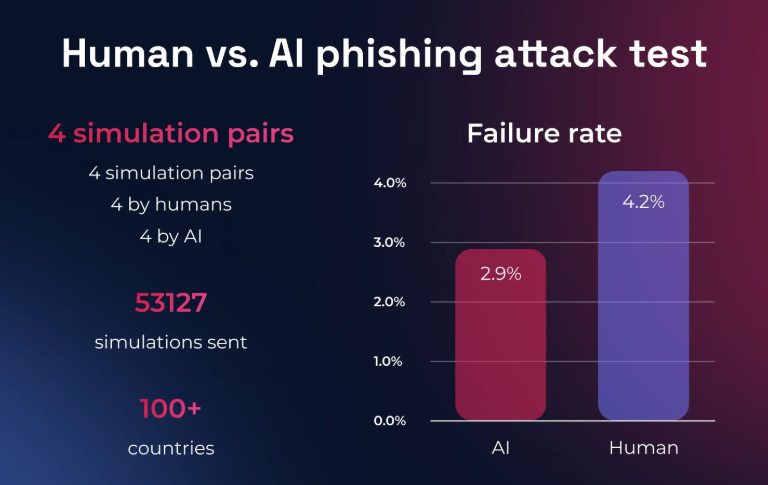
8. AI-Powered Phishing and Social Engineering Detection
Phishing efforts have developed into AI-generated attacks that are extremely targeted. As a result, cybersecurity companies are using AI-driven phishing detection tools that can spot even the smallest language irregularities and photo editing.
These solutions analyze metadata, URLs, sender behavior, and even the tone of communication in real time.
9. Automated Compliance Monitoring and Audit Trails
These days, compliance frameworks like GDPR, HIPAA, and ISO 27001 require ongoing observation rather than merely quarterly audits. Automation solutions create reports that are ready for an audit, monitor the application of policies, and quickly identify non-compliance issues.
In addition to lessening audit fatigue, this improves data governance and transparency throughout the company.
10. Quantum-Resilient Cryptography and Key Management Automation
The field of cybersecurity is shifting toward quantum-resilient cryptographic algorithms as classical encryption faces threats from quantum computing. By 2025, key rotation, certificate management, and smooth encryption protocol transitions are all accomplished with automation platforms.
This guarantees the protection of private information in both classical and post-quantum settings.
Conclusion: Automation at the Heart of Creating the Future
These security automation trends help businesses shift from manual operations to proactive, real-time responses. Automation in security is now essential, not a luxury. With rising threats and shrinking response windows, 2025 will be the year organizations transition from reactive to proactive cybersecurity. Businesses can maintain their resilience, agility, and compliance in an increasingly complex threat landscape by adopting these new trends.
From AI-driven threat response to automated compliance and cloud posture management, automation will define the next generation of cybersecurity operations.