Overview: The Evolution of Cybersecurity Challenges
In today’s evolving digital landscape, SOAR in cybersecurity operations is rapidly becoming essential to handle rising threats like ransomware and insider attacks in today’s digitally-first world. Ransomware, phishing, insider attacks, and zero-day vulnerabilities are all continual risks to organizations. The increasing automation and multi-vectority of hacks make routine security procedures a response time bottleneck. SOAR platforms are at the forefront of the growing adoption of innovative technologies by organizations in order to be resilient. These technologies provide a centralized, automated way to minimize alert fatigue, improve security team procedures, and react to attacks more quickly.
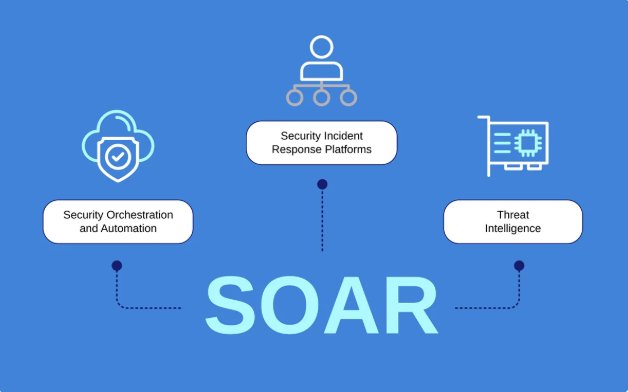
How does SOAR relate to cybersecurity? A Contemporary Security Structure
By integrating threat intelligence, incident management, and workflow automation onto a single The user interface SOAR—an acronym for Security Orchestration, Automation, or Response—is a class of cybersecurity technologies that helps security professionals handle and react to warnings more effectively. Through the use of playbooks, SOAR unifies disparate security tools—such as firewalls, SIEMs, and endpoint solutions—into a single system, freeing up analysts to concentrate on more important decision-making.
Automation is only one aspect of SOAR; context is another. Before taking any action, it adds behavior information, administrative logs, and external information about threats to alarms.
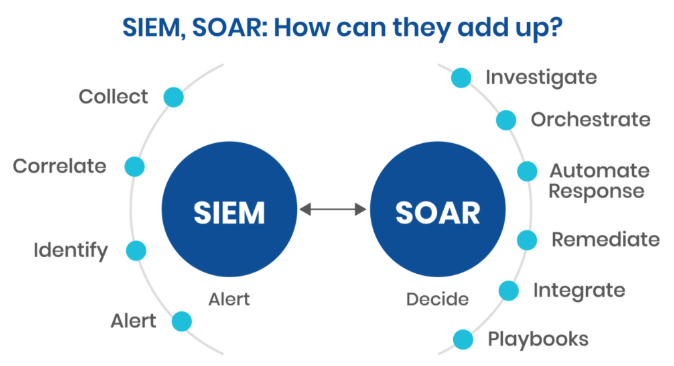
Why SOAR in Cybersecurity Operations Matters
Prior to SOAR, SOC teams had to work under extreme pressure. Daily alert volumes of thousands, analyst bandwidth constraints, disjointed tools, and manual workflows resulted in missed threats as well as reactions that were tardy. Correlating data across tools and reproducing processes at scale were challenging with traditional setups. These issues are resolved by SOAR platforms by:
- Correlating notifications automatically between systems
- Making response playbooks that can be repeated
- Reducing false positives through contextual enrichment
- Mean Time to Detect (MTTD) and Respond (MTTR) Acceleration
This change prevents analyst tiredness while increasing their safety record.
SOAR Platforms’ Main Advantages for Contemporary Cybersecurity
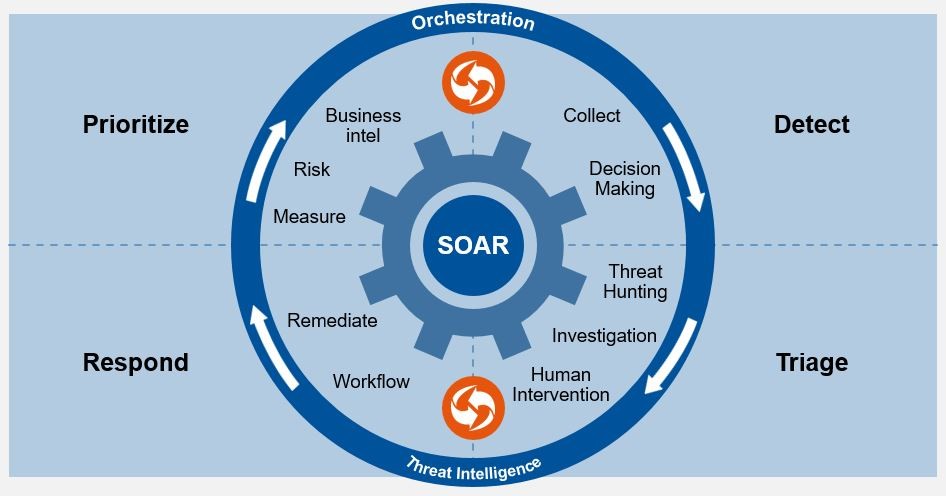
There are observable advantages to implementing SOAR throughout an organization’s whole security lifecycle:
- Response to Incidents Automatically: Respond to incidents in seconds rather than hours with automated runbooks.
- Enhanced Productivity of Analysts: By taking care of routine duties, SOAR frees up qualified staff to concentrate on threat hunting and investigation.
- Threat intelligence that is centralized: Integrate various TI feeds and tools to contextualize alerts before acting.
- Reliable and Repeatable Procedures: Incorporate best practices into playbooks to guarantee adherence to policies and minimize human error.
- Quicker Decision-Making: Rich alerts and automated triage help teams prioritize tasks and take quick action.
How SOAR Works with Other Security Instruments
SOAR improves on current tools rather than replacing them. It has a connection to:
- Security Information and Event Management (SIEMs) are used to extract alerts.
- IDS/IPS, firewalls, and endpoint protection platforms for law enforcement
- Platforms for threat intelligence to enhance context
- ITSM tools to automate notifications and scheduling
This integration enables a centralized command center, removing silos from security operations.
Practical Applications of SOAR in Practice
Use cases for SOAR are as varied as the dangers they are meant to counter:
- Mitigation of Phishing Attacks: Analyzes questionable emails automatically, puts them in quarantine, and notifies users.
- Keeping Ransomware at Bay: Isolates impacted computers, stops malicious domains, and starts forensic procedures upon identification.
- Investigation of Insider Threats: Integrates user logs and information on behavior to identify unusual activities and initiate internal reviews.
- Identifying and enhancing threats: Finds IoCs (the variables of compromise) across entries from many environments, enhancing intelligence.
SOAR Implementation Difficulties (and How to Get Past Them)
Although SOAR has many advantages, putting it into practice can be challenging. Typical obstacles include
- Connecting Legacy Systems: Older tools might not be able to support robotics or APIs.
- Complexity of the Playbook: Designing scalable, accurate playbooks requires a deep understanding of threat response.
- Resistance from the Organization: Teams could be hesitant to entrust important choices to automation.
Strong planning, adaptable SOAR solutions, and starting small—automating low-risk jobs first, then scaling up—are necessary to overcome these obstacles.
Cybersecurity’s Future with SOAR and AI/ML Integration
The development of SOAR is only getting started. Anticipate increased use of AI and ML in a short time to:
- Prioritize and forecast dangers.
- Playbooks that self-adjust according to incident results
- Enhance the detection of anomalies using behavior baselines.
- Offer self-correction with little assistance from humans.
SOAR will probably become a common component of every organization’s cyber defense toolkit as security threats change.
Conclusion: SOAR Is Now Strategic and Not Optional
In a time when threat actors are becoming more sophisticated and quick, mechanical protection is no longer a consideration for enterprises. Security teams can work more efficiently and effectively because of SOAR platforms’ scalable, automated, and sophisticated action layer. The foundation of next-generation SOCs is increasingly SOAR, from alert triage to complete incident remediation. Putting money into it is essential for survival, not simply for efficiency.