Introduction: Why Supply Chain Attacks Have Become a Global Cybersecurity Crisis
In today’s hyperconnected digital world, no organization operates in isolation. Every business—whether a startup, enterprise, or government agency—relies on an extensive ecosystem of vendors, cloud platforms, software libraries, APIs, logistics partners, and managed service providers. While this interconnected environment enables speed, scalability, and innovation, it has also created one of the most dangerous and underestimated cybersecurity threats of the modern era: supply chain attacks.
A supply chain attack occurs when cybercriminals compromise a trusted third party and use that access as a stepping stone to infiltrate downstream organizations. Instead of attacking victims directly, threat actors exploit trust relationships, allowing malicious activity to bypass traditional defenses. As a result, these attacks are often stealthy, persistent, and massively scalable.
Over the last decade, supply chain attacks have shifted from isolated espionage campaigns to a mainstream attack strategy used by nation-state actors and organized cybercriminal groups alike. High-profile incidents such as SolarWinds, Log4j, MOVEit, and 3CX have demonstrated that a single compromised vendor can trigger global fallout across industries. Consequently, understanding supply chain attacks—and learning from real-world breaches—is now essential for cybersecurity resilience, regulatory compliance, and long-term business survival.
What Is a Supply Chain Attack?
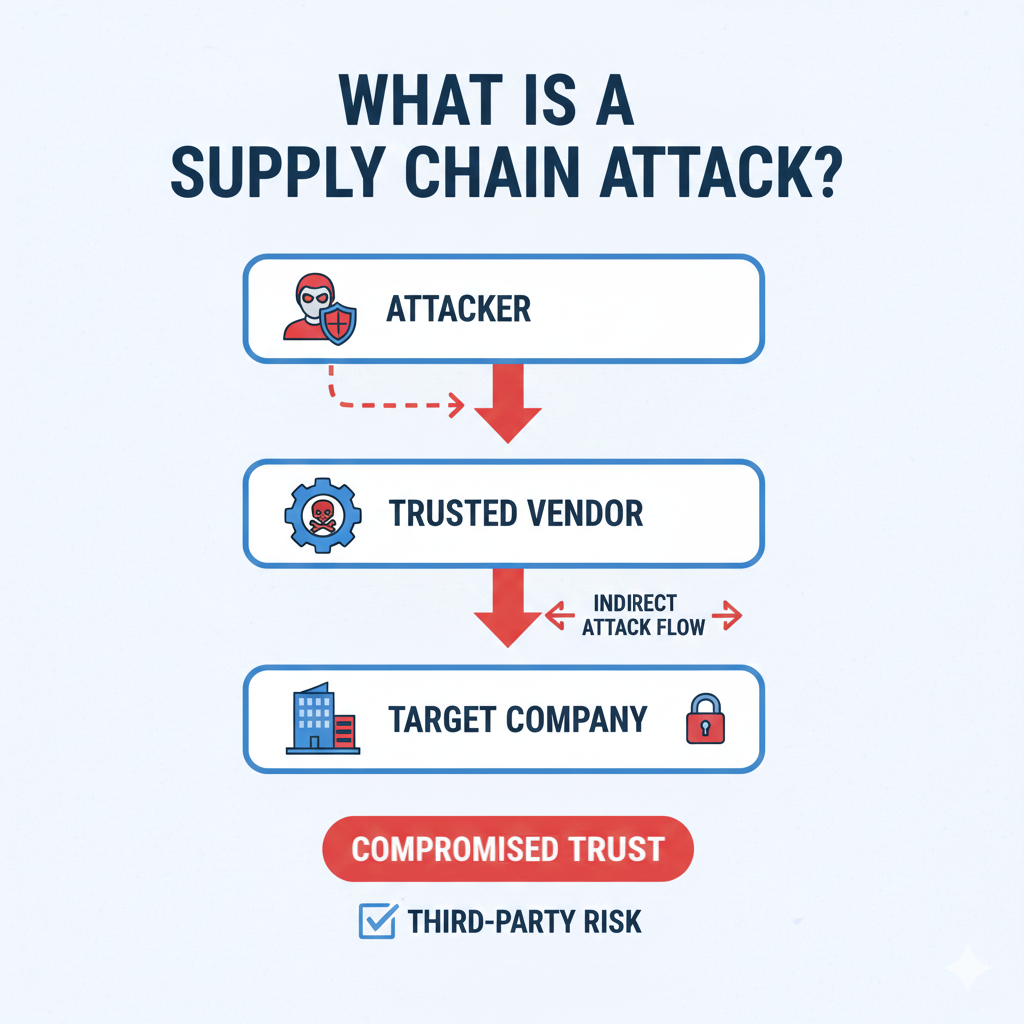
A supply chain attack is a cyberattack in which adversaries infiltrate an organization indirectly by compromising software, hardware, or services supplied by a trusted external provider. These attacks exploit implicit trust, making them particularly difficult to detect and mitigate.
Unlike traditional attacks that target firewalls, endpoints, or employees, supply chain attacks focus on upstream weaknesses. Attackers may inject malicious code into legitimate software updates, compromise open-source libraries, manipulate firmware, or breach managed service providers. Once the tainted product or service is distributed, attackers gain access to multiple victims simultaneously.
Common Entry Points in Supply Chain Attacks
Supply chain attacks commonly originate from compromised software updates, insecure build pipelines, malicious open-source dependencies, breached cloud providers, infected hardware components, and vulnerable third-party APIs. Because these components are deeply embedded within enterprise systems, malicious activity can remain undetected for months.
Why Supply Chain Attacks Are Increasing Rapidly
Several converging trends have accelerated the rise of supply chain attacks. First, modern software development relies heavily on third-party and open-source components, often numbering in the thousands per application. Second, cloud computing has blurred traditional network boundaries, increasing dependency on external service providers. Third, attackers have grown more sophisticated, prioritizing long-term access over short-term disruption.
Additionally, supply chain attacks are highly cost-effective for adversaries. By compromising a single vendor, attackers can gain access to hundreds or even thousands of organizations. From a return-on-investment perspective, few attack vectors offer comparable scale and impact. As a result, supply chain attacks have become a preferred method for both espionage and financially motivated cybercrime.
Real-World Supply Chain Attacks: Lessons from Major Breaches
SolarWinds Orion Attack: A Wake-Up Call for Global Security
The SolarWinds attack fundamentally changed how organizations view supply chain security. Attackers infiltrated SolarWinds’ build environment and inserted a sophisticated backdoor into legitimate Orion software updates. These updates were digitally signed and distributed through official channels, affecting approximately 18,000 organizations worldwide.
What made this attack especially devastating was its stealth. The malicious code remained dormant, evading detection while attackers selectively activated it against high-value targets, including government agencies and critical infrastructure providers.
Key Lessons from SolarWinds: Trust must be continuously verified, build pipelines must be secured with rigorous controls, and monitoring must extend beyond traditional perimeters.
Log4j: When a Single Open-Source Library Shook the Internet
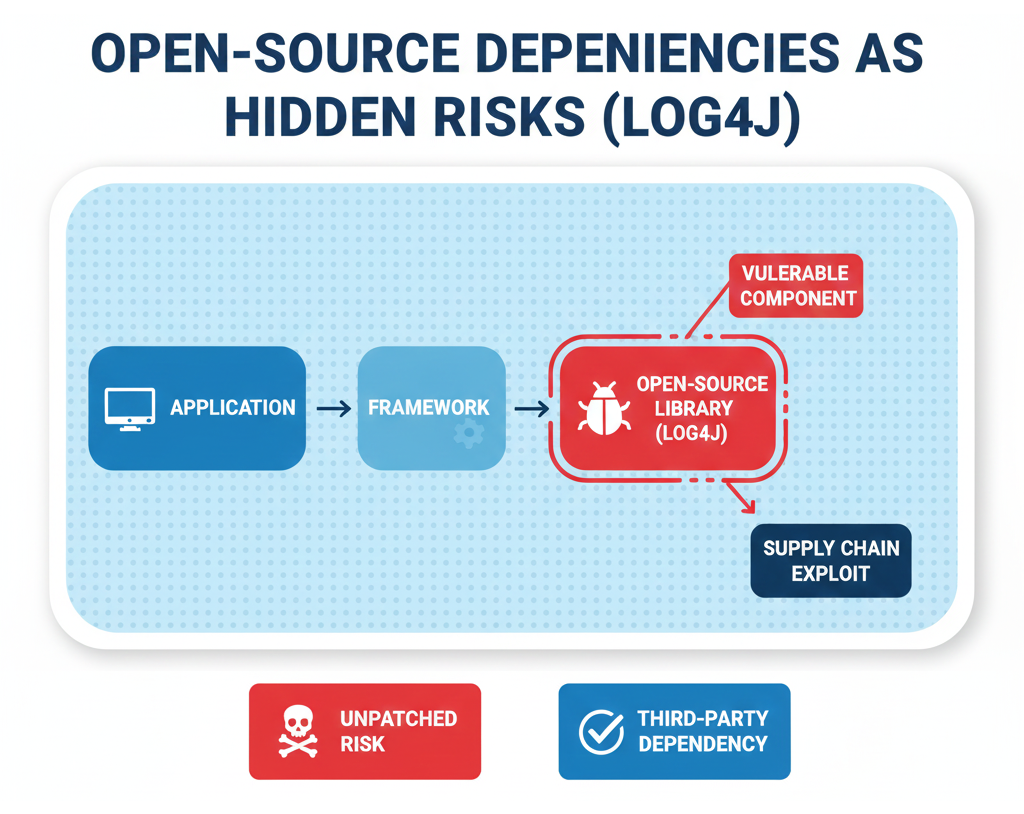
The Log4j vulnerability demonstrated the systemic risks hidden within open-source software. Log4j was deeply embedded across millions of applications, often without developers’ explicit knowledge. When the vulnerability was disclosed, organizations struggled to identify where it existed within their environments.
This incident revealed a critical visibility gap: organizations cannot secure what they cannot see. It also emphasized the importance of Software Bills of Materials (SBOMs) and real-time dependency monitoring.
Security intelligence platforms such as BotDef help organizations detect vulnerable dependencies early and monitor supply chain exposure in real time, reducing response times and minimizing impact.
MOVEit Breach: Centralized Tools, Centralized Risk
The MOVEit breach exposed the risks associated with widely used enterprise file transfer solutions. A zero-day vulnerability allowed attackers to exfiltrate sensitive data from hundreds of organizations across healthcare, finance, and government sectors.
This breach highlighted how centralized third-party tools can become single points of failure. It also reinforced the need for rapid patching, vendor accountability, and continuous vulnerability scanning.
3CX Attack: Trojanized Trust
In the 3CX incident, attackers compromised a legitimate desktop application installer, distributing malware through official channels. Because the software was signed and trusted, many endpoint defenses failed to detect the threat.
Key Lessons: Digital signatures alone are insufficient, behavioral monitoring is critical, and endpoint trust must be continuously validated.
How Supply Chain Attacks Typically Unfold
Despite differences in execution, most supply chain attacks follow a predictable lifecycle. Attackers begin with reconnaissance, identifying vendors with broad customer reach. They then exploit vulnerabilities to gain initial access, inject malicious components, and distribute them through trusted channels. Finally, attackers establish persistence, move laterally, and exfiltrate sensitive data.
Understanding this lifecycle allows organizations to deploy layered defenses at every stage, significantly reducing overall risk.
How Organizations Can Defend Against Supply Chain Attacks
Defending against supply chain attacks requires a strategic, multi-layered approach. Organizations must implement strong vendor risk management programs, enforce Zero Trust principles, and maintain full visibility into their software components through SBOMs.
Additionally, continuous monitoring and threat intelligence are essential. Platforms like BotDef provide real-time detection of suspicious behavior across third-party integrations, helping organizations identify threats before they escalate.
Business, Compliance, and SEO Impact of Supply Chain Security
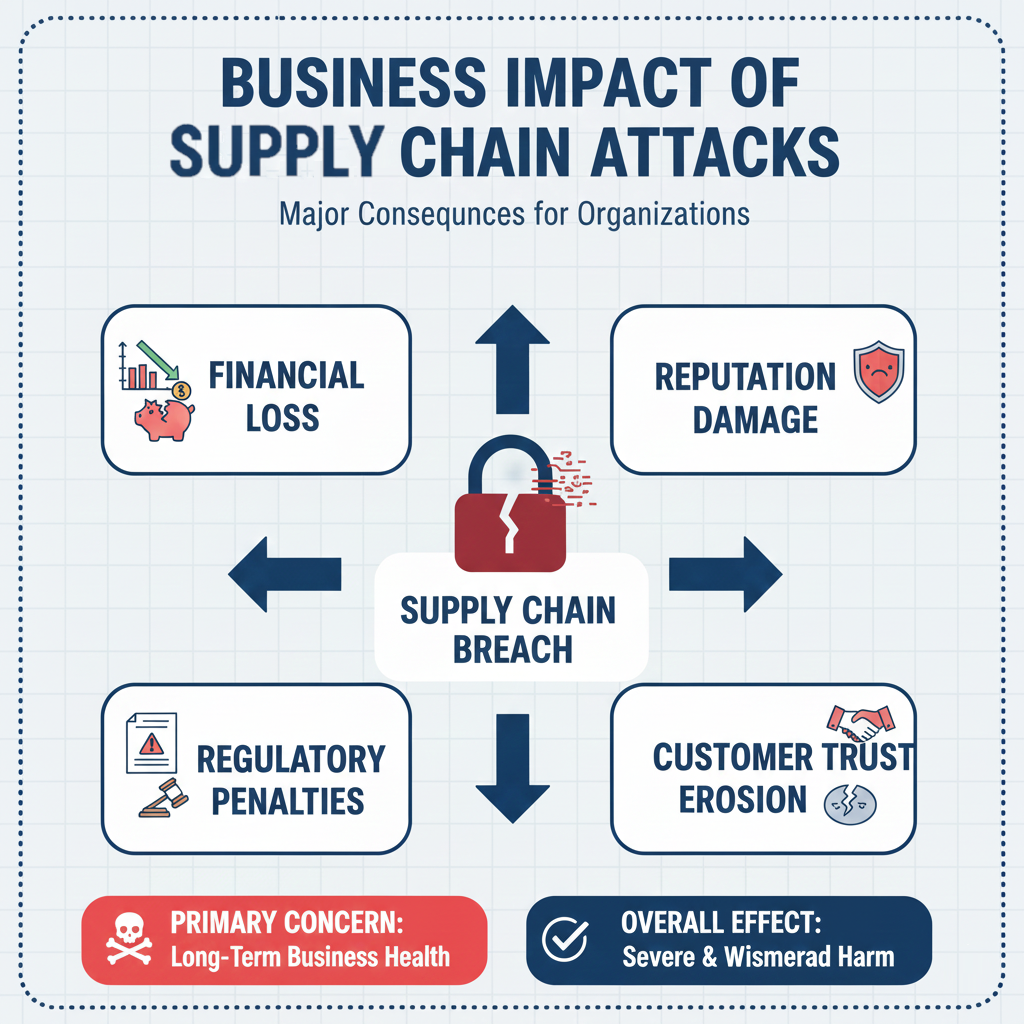
Beyond technical consequences, supply chain attacks cause reputational damage, regulatory penalties, and financial losses. From an SEO perspective, publishing authoritative, in-depth cybersecurity content supports Google’s E-E-A-T framework, improving long-term visibility and trustworthiness.
Well-structured, expert-driven content on supply chain security positions organizations as thought leaders while strengthening organic search performance.
Conclusion: Turning Breach Lessons into Long-Term Resilience
Supply chain attacks represent a fundamental shift in the cybersecurity threat landscape. Organizations must move beyond perimeter-based defenses and adopt ecosystem-wide resilience strategies. By learning from real-world breaches, implementing Zero Trust, maintaining SBOM visibility, and leveraging advanced monitoring tools like BotDef, businesses can significantly reduce exposure.
Ultimately, supply chain security is not just a technical necessity—it is a strategic imperative that defines trust, resilience, and competitive advantage in the digital age.